The Payoff

In May 2016, a hacker seized control of computer systems at Kansas Heart Hospital in Wichita. The hospital could not regain control unless it paid the hacker a ransom—an amount reported to be “small.”
Thousands of other organizations, including a disproportionate number in the healthcare industry, have done the same. No one really knows how many businesses have been hit by ransomware attacks, because they are typically kept private. In most cases, the victims simply pay up, usually in bitcoins, and their computer system is set free.
The ransoms are less than eye opening—usually in the few-thousand-dollar range. This was the case in February 2016 when malware infected some computer systems at Hollywood Presbyterian Medical Center in Los Angeles. The hospital paid a $17,000 ransom (about 40 bitcoins) for the decryption key. Three days later, it regained control of its systems.
But this was not the case at Kansas Heart Hospital. After the hospital payed the ransom, the cyber criminal wanted more. The hospital’s security consultants advised against it, and the hospital had to invest in the time-consuming and expensive task of rebuilding and restoring its computer network.
Welcome to ransomware, the modern-age equivalent of a well-worn extortion scheme in which a small business pays for the release of its hostage—in this case, data.
Computer systems are at risk of being contaminated by malicious software embedded with infected email links, email attachments and compromised web pages. And in the case of hospitals, someone’s health could really be in jeopardy.
Two primary types of ransomware are prevalent today: one that locks up a computer screen so users cannot access their applications and another that leaves applications running but encrypts the files so they can’t be opened. Some of the well-known latter ones are CryptoLocker, CryptoWall, CryptXXX and TeslaCrypt.
CryptoWall alone has fleeced victims of more than $325 million since June 2014.
In both cases, the usual entryway for a cyber extortionist is a phishing scam that encourages or entices computer users to click on something they shouldn’t. Click on it—and POW! The screen locks up and a scary flashing message appears: “You have 96 hours to submit payment. If you do not send money within provided time, all your files will be permanently encrypted and no one will be able to recover them.” (That is an actual ransomware message.)
Most organizations pay up—and who can blame them? In today’s 24/7 business environment, a few days without access to vital operating systems can be financially devastating, if not ruinous. Savvy cyber extortionists appreciate this reality and keep their ransoms relatively low, making the decision to pay pretty easy.
The problem is the FBI has advised the business community not to pay. The nation’s chief law enforcement officials say paying the ransom will embolden cyber criminals to attack other businesses, including the same company twice.
This means many businesses are stuck between a rock and a hard place. If they don’t pay up, they may have to rebuild their systems from scratch at great expense and time. If they do pay up, they’re flouting the FBI’s advisory. Adding to the dilemma is the fact that several insurance carriers now offer cyber policies that cover the cost of paying the ransom, which likely makes payment an even more enticing option.
“It’s an ethical dilemma,” says Matt Chmel, an assistant vice president with Aon Risk Solutions. “Say the organization does pay the ransom, is given the decryption key and keeps the attack private. Then, a few months or even years later, it is publicly revealed that the business had unknowingly paid the ransom to an affiliate of a terrorist organization. Imagine the impact on their reputation and future business dealings.”
Targeting Privacy
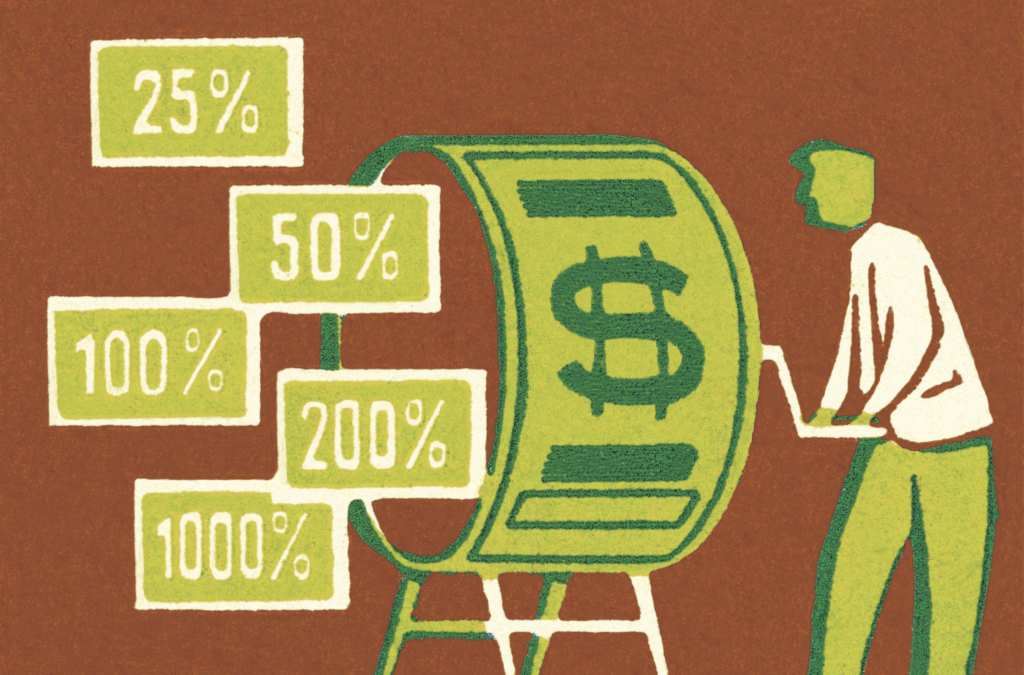
If your business has not been targeted and hit with a ransomware demand, you’re one of the lucky ones. A recent survey of IT leaders at more than 500 companies in four countries indicated that 40% had experienced an attack in the past year. In one of these countries, Britain, 54% of the companies in the respondent pool were hit. Most of the ransom amounts were less than $10,000, although one fifth exceeded that figure and 3% were in excess of $50,000.
Ransomware is rapidly advancing. The Justice Department says attacks quadrupled from 2015 to 2016, averaging an astonishing 4,000 a day. Beazley has also reported that ransomware attacks among its clients more than quadrupled in 2016, with nearly half of these attacks in the healthcare sector, and Beazley projects these attacks will double again in 2017. According to the Justice Department, the U.S. is most affected, accounting for 28% of infections globally, followed by Canada and Australia with 16% and 11%, respectively, according to a report by IT security firm Symantec, which attributes the statistics to hackers’ focus on developed and affluent nations. The service sector is most often successfully hacked, with 38% of infections. Manufacturing is next with 17%.
Healthcare organizations like Kansas Heart and Hollywood Presbyterian are another primary target of ransomware. One study indicates healthcare providers are 4.5 times more likely to be hit by CryptoWall malware than organizations in other industries. Hackers target healthcare providers because of the strict regulations in place to protect patient confidentiality—this provides strong incentive for providers to pay the ransom.
“Hospitals are susceptible to ransomware because of the urgency of healthcare,” says Richard Chapman, chief privacy officer at University of Kentucky HealthCare, a large healthcare provider in eastern Kentucky. “We have patients coming in around the clock, seven days a week. If the computer system goes down for even seconds, it can spell the difference between life and death in an emergency situation.”
Chapman confided that the hospital system has not experienced a ransomware attack. But as someone charged with protecting the privacy of patient medical care records, he is understandably concerned. “Two other hospitals in the state were recently hit,” he says.
Education is another industry in the crosshairs. In the United Kingdom, 63% of universities have been held up for ransom. One school, Bournemouth University, suffered 21 attacks in a single year.
Why target universities? “We have sensitive information on our students that is highly personal, information that may be embarrassing in some cases,” says Reed Sheard, chief information officer at Westmont College in Montecito, California.
Another reason hackers target schools is the state of their technology networks. “Compared to large, well-capitalized business enterprises, universities are easy targets because they have all these legacy systems, are often underfunded and have stretched thin their IT resources,” Sheard says.
Westmont has not experienced a ransomware attack—“as yet,” says Sheard. While he is currently transferring all files related to email, calendars and student grades to the cloud as a loss prevention and mitigation strategy, he acknowledges that even the cloud is vulnerable to cyber criminals. “Phishing is a risk no matter where you store data—on premises or in the cloud,” Sheard says. “You can put in all sorts of guidelines to reduce people’s susceptibility to a scam, but at the end of the day they have to follow them.”
Preventing cyber extortion is not impossible, but it is difficult. That’s due to the increasing sophistication of phishing attacks and the tendency of people to take their chances on what looks real. According to Verizon’s 2016 Data Breach Investigations Report, 30% of phishing emails get opened. Wombat’s 2016 State of the Phish study found phishing attacks had increased by 60%. Email attachments are the primary delivery vehicle for ransomware, followed by infected web pages and email links.
Educating employees about the impact of phishing risks on the business can help lower these percentages. Employees must be made aware how critical it is not to click on a link without scrutinizing the legitimacy of the email. To put teeth into the training, try ethical hacking, sending an infected email to employees to see if they click.
In such cases, the duped user can be required to take additional hours of training.
Jerry Irvine, of the U.S. Department of Homeland Security’s Cyber Security Task Force, says security applications such as VectorShield, which are inserted into a browser to immediately encrypt a user’s browser session once it is hit by ransomware, are very useful.
“The app instantly infects that session to destroy just those malicious files. This way the malware doesn’t hit the rest of the system,” Irvine explains. “It’s just one of many network segmentation strategies to set up walls within the systems to limit the infection to that one segment.”
Irvine advises users to immediately unplug the computer, disconnect all peripherals and other connected devices, and remove the thumb drives. “The goal is to get the infected system quickly off the network.”
A well-considered disaster recovery plan lays out best practices, controls and procedures, arguing for the assistance of a security consultancy. Testing the controls and procedures on a routine basis will ensure everything is working.
Lastly, it can be helpful for all businesses to collectively and anonymously contribute their experiences to law enforcement agencies and industry organizations battling the scourge. For example, websites such as Europol’s No More Ransom will help a business regain access to its encrypted files or locked systems—in some but not all cases—obviating the need to pay a ransom. The organization has created a repository of encryption keys and applications assembled from previous hacks that can decrypt certain types of ransomware.
The FBI is another source of encryption keys and applications, says Alan Cohn, a former assistant secretary for strategy and planning at the Department of Homeland Security who is now counsel at international law firm Steptoe & Johnson. “Since all of us are vulnerable to ransomware attacks, we have a common cause in coming together to defy it,” he stresses. “Insurance brokers and carriers are part of this common cause, as they have a commercial interest in mitigating these risks to the greatest degree possible.”
Working collectively, businesses would be in a better position to thwart the extortionists than any individual company can on its own.
The Business of Ransomware
Roughly 43% of ransomware victims are unsuspecting employees hooked by hackers in a phishing scam. By far, phishing attacks are the major method of reeling in a gullible victim. In fact, 93% of phishing attacks now contain encryption ransomware, almost double the percentage in 2015.
The successful attacks have resulted in an explosion in phishing emails, which reached 6.3 million in the first three months of 2016, a stratospheric 789% increase over the last quarter of 2015.
Practice makes perfect, and this is increasingly the case with ransomware. Hackers are leveraging more sophisticated techniques, as demonstrated in recent cases studied by Symantec, “displaying a level of expertise similar to that seen in many cyberespionage attacks,” the firm states. For instance, hackers have developed user-friendly Ransomware-as-a-Service (RaaS) variants that anyone with a little cyber know-how can deploy from a home computer, acting as a de facto agent for these criminal organizations. The person simply downloads the ransomware virus and perpetrates a phishing scheme. If the victim pays up, the agent gets a commission.
Other enhancements include extending the scams beyond infected email links, attachments and web pages. “We’re seeing adware pop-ups being added to the list of phishing scenarios,” says Jerry Irvine, a member of the U.S. Department of Homeland Security’s Cyber Security Task Force and CIO at IT technology firm Prescient Solutions. “The hacker knows you like shoes and sends you a pop-up offering a discount. You click on it and inadvertently download ransomware.”
In many ransomware attacks, the hackers are extremely businesslike. The reason is clear: not many organizations are knowledgeable about bitcoin payments, as they have not had any commercial reasons to traffic in the digital currency. So the hackers do what they can to help. “Their customer service is phenomenal,” says Robert Boyce, industry affairs associate at the Council of Insurance Agents & Brokers. “They’ll assist the victimized business through the bitcoin process, sending helpful links on how to pay. It’s become a business.”
To Pay or Not to Pay
When weighing whether to pay up, considerations range widely. “If you don’t pay a $10,000 ransom, the attack could end up costing an organization millions,” Chmel says. “You have the cost to rebuild the network, then you’re down for who knows how many days. You now have to contact your key partners like suppliers and banks about the situation, as well as all your customers, whose orders may now be stalled.”
On top of the business interruption costs, companies also must deal with the expense of hiring a technology forensics firm to assess the breadth of the infection caused by the malware and may also need a crisis management firm to handle the public backlash. In addition to these tangible expenses, companies also confront reputational damage. Existing customers may think twice about continuing to do business with a company knowing that its IT systems were vulnerable. In many cases, the simplest solution is to pay up and keep mum.
There’s another factor that argues in favor of paying the ransom—D&O liability. “Many company directors and officers are worried that if there is an incident and they don’t pay the ransom, they may face liability for not adequately protecting the organization to avoid the catastrophic financial events that occurred in its wake,” says
Dan Twersky, assistant vice president and claims advocate at Willis Towers Watson.
A 2016 survey found businesses affected by ransomware endured an average of three days without data access. “The downtime could lead to business losses affecting the financial stability of the entity,” Twersky says. “Attorneys will argue, ‘Here was an opportunity to avoid a catastrophic event by simply paying what is a pretty nominal fee being demanded.’ And that has certainly been the way most of our clients are ultimately reacting to these events.”
Not that the decision is by any means easy. Take Methodist Hospital in Henderson, Kentucky, for example. It revealed in March 2016 it was in an “internal state of emergency” following encryption of its files by a malware variant known as Locky Crypto-Ransomware. The hospital declined to pay the small ransom demand (four bitcoins, about $1,650 at the time), reportedly shutting down the infected parts of its network and relying on stored backup copies of most files to continue operations. It took five days to get the systems back up and running in their normal state.
Fortunately, the disruption did not affect patient care or patient information, which remained secure in a backup system while the main network was locked down. By acknowledging the attack and its timely response, the hospital also reduced the impact of reputational damage. Nevertheless, five days offline likely had some financial impact on the hospital. In other industry sectors, a lost week could be devastating.
Asked if he would have the same response to a ransomware attack, University of Kentucky HealthCare’s Chapman was uncertain. “I know the FBI advises against paying the hackers,” Chapman says, “but not being in the situation I can’t say what we would do.”
“As long as this continues to be a viable source of income, the bad guys will continue to do it,” says Julie Bernard, principal in the cyber risk services practice of Deloitte Advisory.
Another worrisome issue for many is the possibility a ransom payment may flow to affiliates of a terrorist organization like ISIS or Al Qaeda. Terrorists are keenly interested in ransomware, given the potential for large-scale business disruptions and economic dislocation, as well as access to an easy source of capital. If it leaks out at some point that a business has paid ransom to a terrorist group, the business could sustain severe damage to its reputation.
To pay or not to pay suddenly takes on Hamlet-like confusion. Many technology experts, such as Alan Cohn, a former assistant secretary for strategy and planning at the Department of Homeland Security, are firmly in the latter camp but appreciative of the complicated decision. In his view, cooperation with the government is essential.
“Law enforcement agencies understand the vexing nature of ransomware and are much more likely to look favorably upon victims that are cooperative, even if a ransom has been paid,” says Cohn, now counsel at international law firm Steptoe & Johnson.
What are brokers recommending to clients who express these concerns? “We don’t formally advise them to pay or not to pay,” Aon’s Chmel says. “We tell them the pros and cons for doing one or the other and leave the determination of what to do up to them.”
The availability of insurance to transfer the ransom and related business interruption expenses to an insurer certainly complicates the decision. Several insurance carriers cover cyber extortion, though it is not yet available on a stand-alone basis. As an insuring agreement, it is an optional tag-along to the wider cyber risk/data breach insurance product, with an annual aggregate sublimit of financial protection and an annual aggregate deductible. The boilerplate in most covers the cost of the ransom paid to meet the extortion demand, the expenses paid to hire computer security experts to prevent future extortion attempts, and the fees paid to professionals to negotiate with the extortionists.
Within the more comprehensive data breach policy are other risk transfer products and services, such as credit monitoring, forensic investigations, and crisis management. All of these coverages may be needed for companies to truly sleep easy. However, the devil is in the details.
“Some cyber extortion insuring agreements may not cover the loss if the underlying cause is a phishing email received by an employee who is at fault for clicking on the infected link,” The Council’s Boyce says.
Chmel notes some agreements also exclude payment of the ransom in bitcoin. Obviously, both exclusions may make the policies less valuable than the paper they’re printed on—hence the need for scrutiny. “If the policy is placed properly by a broker with expertise in this area, it should respond,” Chmel says.
Insurance as a Solution
Brokerages as well are at risk of a ransomware attack. “The important thing is to be educated and informed on the possible causes of loss,” says Boyce. To arm against possible attack, he advocates asking a series of “What if?” questions. Senior leadership within a brokerage—the CEO, CFO and CIO, for instance—should ask about the potential impact of an attack on systems like HR or the finance and accounting. This analysis will foster the development of risk mitigation tactics, such as walling off the system from other systems in the network.
Another benefit of this evaluation is that it will assist brokers with leveraging their own cyber risk analyses on behalf of clients. In collaboration with their insurance markets, brokers can provide extremely valuable cyber-risk services. “The insurance industry plays an important role in modeling, reducing and transferring risks,” says Rep. Ed Perlmutter, D-Colo. “This is why the data breach insurance market has begun to take off in the last several years.”
Perlmutter has a point. After years of dabbling in cyber insurance, the insurance industry now has some historical data to underwrite the risks more closely. Competition in the growing market is another benefit for brokers and their buyers, generating more realistic pricing and more flexible terms, conditions and self-insured retentions, Chmel says.
Cyber insurance has become so important in preparing for and mitigating cyber attacks that Perlmutter introduced a bill last September (H.R. 6032) to provide buyers a 15% tax credit on the premium they’ve paid for data breach coverage. “The legislation will help small- and medium-size businesses realize they should take these threats seriously and utilize the insurance industry as a resource,” Perlmutter says. “The increase in cyber attacks will only result in more disruptions, expenses and reputational costs.”
The goal of the bill is to encourage small businesses to boost their cyber security. To qualify for the tax credit, buyers must have adopted and be in compliance with the Framework for Improving Critical Infrastructure Cybersecurity, published by the National Institute of Standards and Technology, or any similar standard specified by the Internal Revenue Service.
As the bill and the improvements in the industry’s cyber risk coverages indicate, insurers are playing an increasingly important role in helping smaller businesses that might not have the resources to fortify their networks on their own. “It’s time we realize the national security implications,” Perlmutter says, “and use the insurance industry as a part of the solution.”
For ideas on how to do battle with ransomware, check out these websites:
Hackers are targeting companies with an IT skills shortage.
The seemingly universal problem of attracting and retaining skilled workers is a headache that can reduce efficiency, hurt morale and eat into the bottom-line. But when it comes to having enough IT and cybersecurity, where the talent gap is much higher than in the workforce at large, the consequences can be far more dire.
The Center for Strategic and International Studies, a respected Washington think-tank, sized up the shortage and the problems caused by it in a study for Intel that surveyed hundreds of IT managers and professionals in the United States and seven other countries.
“The continued skills shortage creates tangible risks to organizations, and companies say they have already incurred damages as a result of this workforce gap,” CSIS warned in Hacking the Skills Shortage.
Indeed, simple word or rumor of a company’s IT skills shortage alone can lead to cybercriminals sniffing around. More than a third of those surveyed said “their organizations, unable to maintain adequate cybersecurity staff, have been targeted by hackers who suspect a shortage of cybersecurity skills at their organization,” CSIS said.
The survey also reported the following:
- 25% of respondents said their companies had lost proprietary data in cyber attacks
- 22% believed they had suffered reputational damage as the result of attacks
- 17% said the skills shortage had reduced the ability of their company to create new products and services
CSIS said the ultimate solution to the skills shortage is to dramatically increase the number of people educated and trained as cybersecurity experts. That may sound obvious, but the report said the current educational infrastructure is incapable of turning out a much larger and steady stream of IT pros.
“Simply put, most educational institutions do not prepare students for a career in
cybersecurity. Our research suggests that cybersecurity education should start
at an early age, target a more diverse range of students, and provide hands-on
experiences and training,” CSIS said.
“Most institutions of higher education do not offer cybersecurity concentrations and do not guide graduates to cybersecurity professions,” said the report.
CSIS urged universities to work with employers and the government to craft curricula based on real-world needs. “Programs should focus on hands-on learning in the form of labs and classroom exercises to provide people with robust and practical skills in this field,” it added.
While schools and colleges develop a more robust program, employers should consider relaxing degree requirements for entry-level cybersecurity workers “and place greater stock in professional certifications and hands-on experience for evidence of suitable skills.”